Prevent data vulnerabilities in
on-prem shared folders

.png)
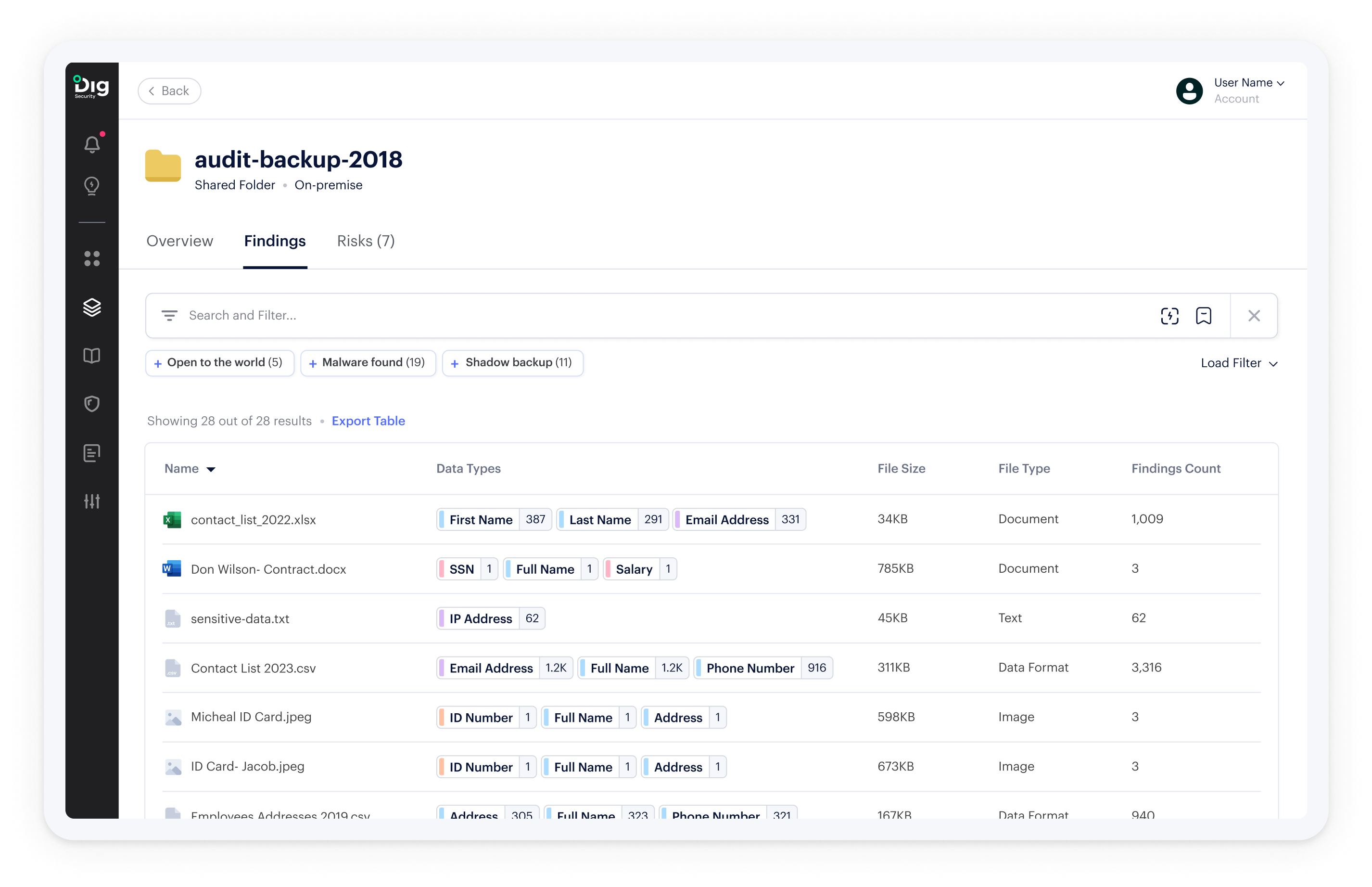
Gain visibility into data and permissions across millions of documents shared in SMB, FTP, and NTFS folders
File shares accumulate millions of documents, a fraction of which will contain sensitive data such as trade secrets or employee details. Labeling and naming conventions for these files are often poorly enforced or documented; nested permissions to folders and files can be nearly impossible to untangle. As a result, businesses are unable to answer the key security questions around sensitive data, access, and exfiltration.
Dig scans and classifies the documents in your on-prem file shares. And we give you immediate insight into the topography and governance of your shared folders – so you can improve your security posture before, after, and during your cloud migration.
Security Scenarios
Understand how Dig defuses common data security risks in on-prem shared folders.
A legacy HR system periodically exports CSVs containing employee records into a shared folder
Risk
Exposure of employee PII, compliance violation
Dig Solution
Identifies the sensitive data stored in the CSV files, maps permissions, and highlights the relevant compliance frameworks
As part of a digitization project, photocopies of documents containing sensitive customer data are uploaded into a file share
Risk
Potential for data exfiltration, compliance violations
Dig Solution
Identifies the sensitive data via OCR, and monitors access to the relevant document or folder
A large group of users in the organization is granted access to a folder containing trade secrets
Risk
Leak of sensitive information, insider attacks
Dig Solution
Alerts security teams to the new permissions being granted, and highlights the risky documents that were shared
Security Scenarios Dig Solves for Customers
Understand how Dig defuses common data security risks
Shadow backups on S3
Security Risk
A database containing PII has been replicated to an unencrypted S3 bucket, which isn’t managed by the central engineering organization
Dig Security Solution
Dig automatically discovers the S3 bucket containing the shadow backup; classifies any sensitive data contained in the backup; determines the risk level (compliance violation); and alerts the security team.
Sensitive data on unmanaged data store
Security Risk
To test a new use case, a developer has spun up an EC2 machine, installed a PostgreSQL database on it, and loaded customer data into the database.
Dig Security Solution
Dig identifies any virtual machine that has a database installed on it; scans and classifies the data within the PostgreSQL instance; and alerts the security team that sensitive data is being stored in an unmanaged database.
Data exfiltration
Security Risk
An orphaned snapshot of an unused database,
which has not been accessed for a long time, is now being shared with an unfamiliar account.
Dig Security Solution
Dig identifies the breach in real time and alerts security teams, which can take steps to contain the attacker and prevent further data loss.
How it Works
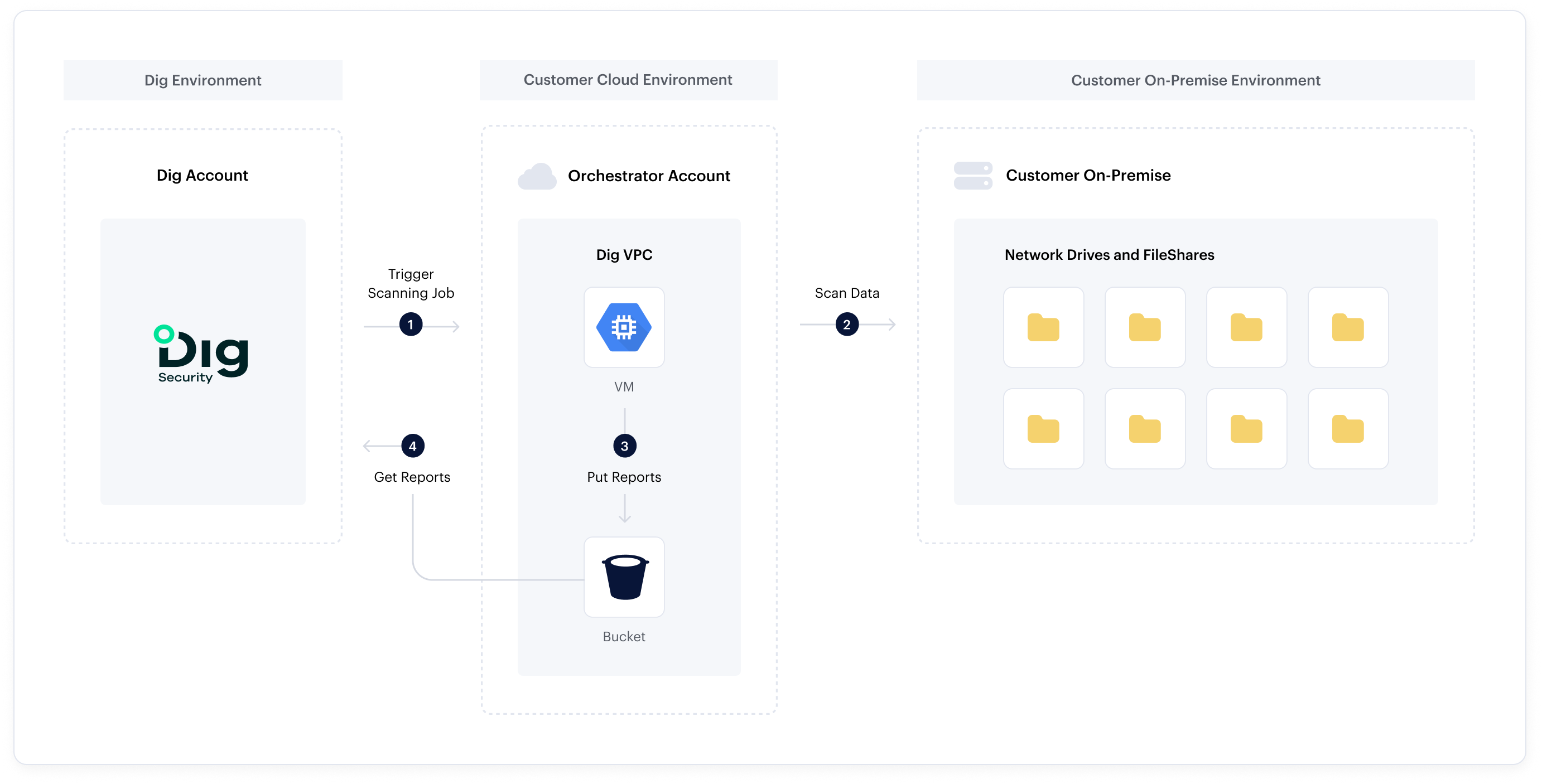
Dig Protects Your Data Everywhere
On-premises file-shares is just one piece of the puzzle.
Make data security an integral component of your cloud strategy
Schedule today a call with an expert. We’ll help you understand the current threat landscape, and discuss ways to reduce the risk of a data breach.
Let’s Talk